3 min read
One-Click access to servers and VMs with Session Manager and MontyCloud
 Luke Walker
:
Jun 18, 2020 11:49:00 AM
Luke Walker
:
Jun 18, 2020 11:49:00 AM
This post originally featured in the AWS Management & Governance Blog
IT administrators and DevOps engineers often perform routine operations to manage their cloud infrastructure, modern on-premises environment workloads, and applications. One such routine operation is the ability to manage Amazon EC2 instances, on-premises instances, and virtual machines (VM) through a remote session. Several tasks such as application and server log reviews, fine-tune configurations, or aborting runaway processes are performed with session access.
In this blog Luke Walker, principal product manager at MontyCloud, describes how customers and APN Partners can use MontyCloud’s DAY2 solution to enable one-click-controlled access to instances via AWS Systems Manager Session Manager.
Overview
Customers typically configure secure access to sessions by using bastion hosts, SSH keys and similar administrative protocols. Set up and ongoing maintenance of bastion hosts, while administering SSH ports, or managing usernames and passwords requires specialized skills and takes additional time. With AWS shared responsibility model, customers are responsible for these operations, which adds additional burden of risk, and effort to maintain security standards.
Session Manager provides a browser-based interactive shell and command line interface access for managing Windows and Linux EC2 instances, without the need to open inbound ports, manage SSH keys, or use bastion hosts. Administrators can grant and revoke access to instances through a central location by using IAM policies. This allows you to control which IAM users can access each instance, including the option to provide non-root access to specified users. Once access is provided, you can audit which IAM user accessed an instance and log each command to AWS CloudTrail, Amazon S3, or Amazon CloudWatch Logs, respectively.
MontyCloud DAY2 (DAY2) helps customers achieve one-click, secure, and auditable access to sessions for Windows and Linux instances. Because DAY2 is built on top of Session Manager, it eliminates the need for bastion hosts or SSH ports to be opened and instantly saves time, costs, and significantly increases the security posture for customers.
Managed service providers and APN Partners see much value in this feature. For example, we are working with AFour Technologies (AFourTech), a Redmond, WA-based software development and reliability engineering services company. AFourTech works with several leading SaaS companies to help accelerate feature development and to manage their CI/CD pipelines on AWS. Typically, AFourTech’s IT administrators set up hundreds of development and QA systems on EC2 (EC2) instances, within a customer’s domain.
With DAY2 and AWS Systems Manager Session Manager, AFourTech is able to instantly launch remote sessions for the EC2 instances under management.
“Our ability to launch a remote session right out of the MontyCloud application is very impressive and gives agility to IT admins who need to quickly connect to multiple hosts under the same pane of glass without having to work with keys/credentials. We typically set up multiple Dev, QA systems with specific software versions, patch levels which requires validation where this comes handy. This is further protected by the predefined cloud roles and logged with remote access history, making it secure.”~ Venkatesh Deshpande, Head of IT Operations, AFourTech
Configuration
DAY2 automatically configures the required IAM roles and policies to support the feature set as part of your AWS account onboarding process, but before we can open our first console session, we must first make sure that our instances are managed by AWS Systems Manager.
We can see the status of all instances discovered by opening DAY2 and navigating to Infrastructure. This displays all instances across accounts and Regions.
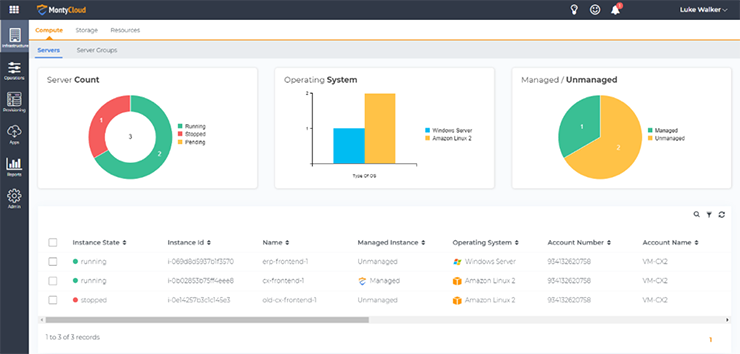
The instance we want to start a session with, erp-frontend-1, is not managed. To gain easy access to the machine, select the instance name, then from the context menu click Convert to Managed Instance and accept the prompt in the dialog box. This launches the conversion process and activates the Systems Manager agent.
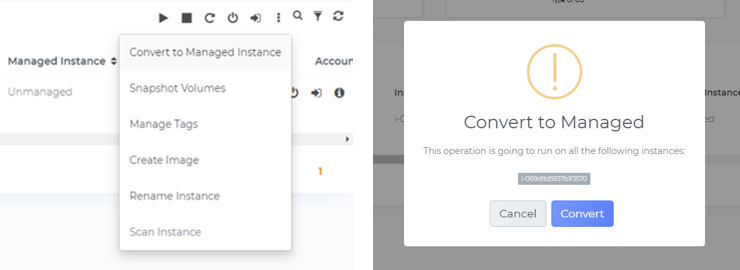
The Systems Manager agent itself is preinstalled by default on instances created from AWS Windows Server, Amazon Linux and Linux 2, Ubuntu Server 16.04/18.04 and Amazon ECS-Optimized AMIs, but if the agent is not available within your AMI, you must manually install the agent first.
Once the instance is managed, we can move to opening a session. Navigate to the instance and select Remote Session.
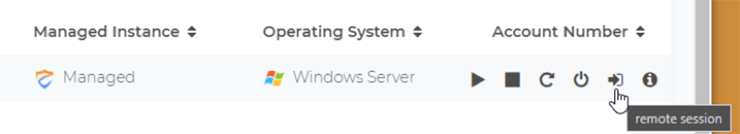
A new dialog box appears, and the PowerShell session begins for the Windows instance immediately:
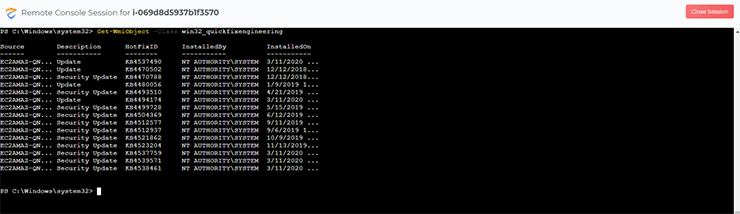
We can do the same for my managed Linux instances:
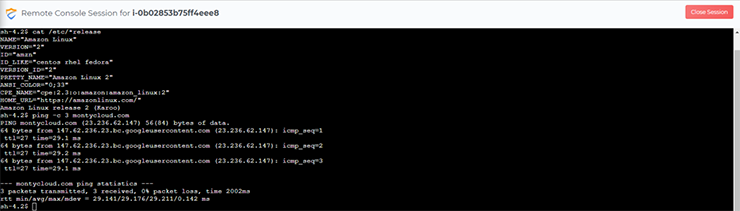
Now that we have demonstrated how to easily manage and gain shell-level access to your EC2 instances, a common task is to review a previous session to capture the output for troubleshooting purposes, or to audit the commands issued by a user.
By accessing the Info panel of the instance, we can see a list of all recent sessions:
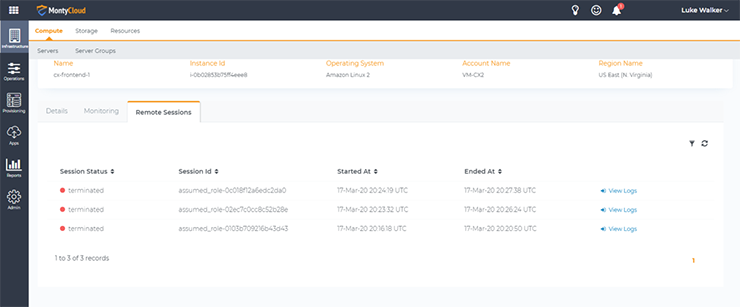
We can then access the recorded session to review the commands issued by the user, and the output they received:

Conclusion
With Session Manager and DAY2 you can
- Use native tooling from AWS Systems Manager, and rely on high availability and secure access for critical operations
- Access Windows and Linux instances directly, without the need for bastion hosts or exposed SSH/Remote PowerShell ports, decreasing the risk of brute force attacks.
- Get one-click web-based access that removes the need to deploy and manage local tooling and key management across your workstation fleet.
- Avoid the risky practice of sharing keys and improve security by eliminating the need to configure user accounts and passwords.
- Deliver auditability with full fidelity logs of all remote sessions and activities.
To learn more about this feature and MontyCloud’s DAY2 intelligent Cloud Management Platform, please go to https://www.montycloud.com.


